Security - Getting Started
I did some polls and surveys recently, which indicated that security and hardening might be important issues for some of you. This article marks the start of a series about these topics.

I did some polls and surveys recently, which indicated that security and hardening might be important issues for some of you. This article marks the start of a series about these topics.
I want to provide some ideas, configurations, and practices that I learned in the past. Be aware, that I cannot cover everything. Instead, I will focus on things that might come handy on a regular basis, without digging too much into one direction.
Introduction
The series is addressing security and hardening patterns. The below articles are based on a scenario, provided in the "Security - Getting Started" article.
- Getting Started
- Physical Security
- Data Security
- Network Security
- Transport Security
- Session Security
- Presentation Security
- Application Security
- The human layer
For this article, we will have a look at the used framework, and the example scenario and the used software.
Important Notice
No system is exactly the same and can be treated the same way. Some services are available as a public service, others are not. Furthermore, the article series will talk about some measurements, but these alone will not guarantee security of your system.
Additionally, you cannot become a security expert by learning a couple of tools and running them. Instead, you need to understand different technologies. The above layers may give you some hints where to dig deeper.
Framework
To give you an idea how the articles will be structured, I came up with the below layers and actions. The combination of both allows you to apply >30 actions to the below scenario. Each of the actions may contain multiple steps, too.
And yet, this is only the beginning of your journey in security and hardening patterns.
Layers
Everybody with a network background has already seen the layers we are using. Take a glance at the table of content and take a guess. Got it?
Right, this looks a lot like the Open System Interconnection (OSI) model.
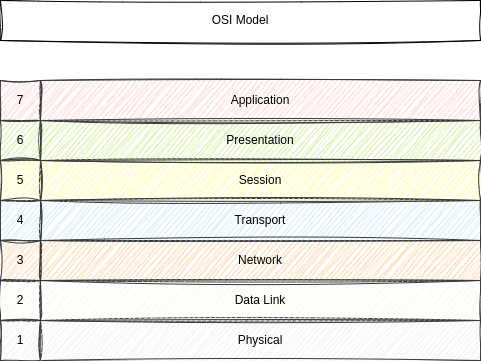
But, we are not limiting ourselves to network connections. Instead, we use a way broader definition. This means, our physical security will tackle all physical assets like servers, switches or other hardware. The same can be said about the data layer. Instead of focusing on data links, we will talk about data management in general.
I really hope this makes some sense, and you can check out the layers that are most interesting to you.
Actions
Each of the following articles will also follow a pattern. In general, we will discuss the below scenario, in the context of the above layers and talk about the following topics.
- Assess (Discovering assets/Inventory)
- Analyze (Getting information about possible attack vectors)
- Action (Implementing security measurements)
- Automate (Making things magic)
- Audit (Reviewing changes and getting reports)
Funny, all the steps are starting with an "A". This really happened by coincidence and might turn out to be a good reminder.
Anyway, for each of these topics, we will have a look at some tooling and come up with some practices to harden the layer. This might look like the below bike example.
Asses
We have one bicycle, used for commuting to work. We don't know the exact price of the bike, but a replacement will cost us ~€500.
Analyze
The bike can be stolen (physical theft) at home (it is also locked in the basement) or at work (a public parking space). A thief may use the bike for driving or selling purposes. The bike is pretty old, but still has some value for us, since we are using it daily. In case it is stolen, we will need to replace it (€500) and need to buy bus tickets to go to work (~€5).
The theft rate for bikes is pretty low in our region. Overnight parking seems to be the biggest attack vector.
Almost all bike specialists consider a bike lock 10-20% of the bike price reasonable. In addition, one can buy trackers, insurances and more.
Action
To protect the bike from theft, we will buy a lock. This lock will protect the bike in a public parking space, but is also used at home, since the bike is parked there, overnight.
Automate
Automating the lock/unlock process is not possible with our budget. There are automatic and smart locks, but these are expensive and have their own attack vectors. But we can set up some kind of reminder. We set up this reminder in our smartphone. Every time we arrive at home, we will be reminded to lock the bike, the same can be done for work.
Audit
We will subscribe to the local newsletter to get information about bike thefts in our region. In addition, we will subscribe to "The daily lock" to get information about malfunction locks or news about new attack vectors/hacking methods for our lock.
We will also inspect the lock on a regular basis, to ensure that it is not scratched or rusty.
Scenario
A series about security can have hundreds of perspectives. You might need to secure your Linux server, your network, your web application or your remote access. You can put security into your development cycle, but also mitigate possible security issues with other tools.
The following scenario will be our template.
I want to host a Nextcloud service in a private network, with public access on a RedHat-family Linux system. The service will be used from me, my family and some friends. Since the service might hold critical data like contacts, private photos or my CV, I want to ensure a high security standard.
In a drawn picture, you might think of something like this:
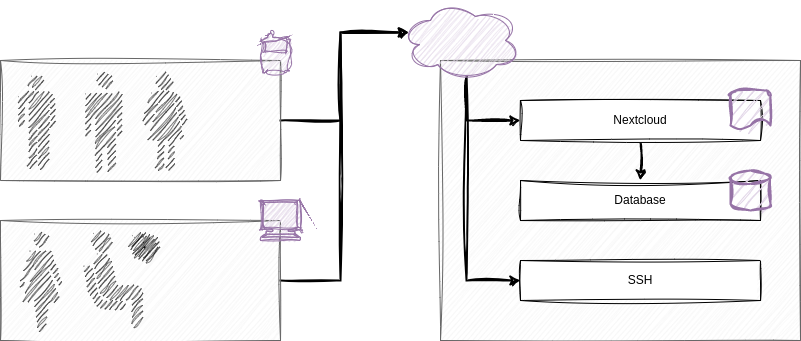
You might think, that this is an easy one. "Just install some random Linux, follow the Nextcloud guide, and done." Right? Well, no.
We will have a look at firewall rules, login to the system, TLS encryption and intrusion detection. We will talk about network separation, brute-force prevention, disaster recovery and privileged access.
In the end, our system will have several security and hardening patterns applied and also report to us. If you are still not on board, we will do this stuff with containers and the setup will be fully automated.
Conclusion
Let's stop it here. In the next article, we will talk about physical security, why it is important and how you can take your first steps in security.
In case you are missing something, want to take a more advanced look in one of the topics, I highly appreciate contact via E-Mail, LinkedIn and Mastodon.